1. Use face ID, touch ID, or a secure passcode

Chances are, you’re already using some method of verification to unlock your phone – whether this be Face ID, your fingerprint, a pattern you have to enter, or a PIN code.
However, since this is your first line of defence against unwanted people accessing your phone, it’s important to get right.
No authentication method is inherently better than any other, otherwise your smartphone manufacturer would only offer you one way to unlock your phone. For example, Face ID can be fooled by a photo on some old Android devices. However, biometric authentication is generally recommended for most people, as it’s normally more secure than using a PIN or passcode.
If you use Face ID on Android, ensure to turn up the settings to the strictest option, to reduce the likelihood of the system being tricked by a photo of you. Then, lock your phone and test it with a photo, to ensure it’s secure.
If you use a passcode, PIN or pattern, ensure that it cannot be guessed. Never use your date of birth or pet’s name, for example. It’s best to think of a completely random PIN and then memorise it, to ensure it can’t be guessed.
2. Ensure “Find My iPhone” or “Find My Device” is set up correctly
Following on from the above tip, if your phone is lost or stolen, you want the ability to either find and retrieve it, or wipe it remotely to ensure that the thief can’t access any information on your phone.
To locate or wipe your phone remotely, you need to ensure that this is set up beforehand on your phone.
- On iPhone, ensure that GPS is turned on. Then go to Settings > your name > Find My > and tap the Find My iPhone slider.
- On Android, ensure that GPS is turned on. Then go to Settings > Security > Find my device and turn it on.
If you ever need to locate or wipe your phone remotely, either go to icloud.com/find or Google “find my device” if you have an Android.
3. Keep apps up to date
App developers constantly release updates to improve their apps’ performance – for example, making them run better on new devices, and releasing new content.
However, these updates also help to improve app security. Therefore, it’s a good idea to keep your apps up-to-date.
To do this, it’s best to enable automatic updates over Wi-Fi, so that you don’t have to worry about keeping apps up to date.
- On iPhone, go to Settings > iTunes & App Store > Automatic Downloads and turn on App Updates.
- On Android, go to the Google Play Store > tap your profile icon in the top right > Settings > General > Auto-update apps.
If you’re concerned about your phone potentially slowing down when updating, and want to perform updates manually, you can also do this from the App Store or Google Play store.
4. Keep your operating system up to date
Similarly, operating systems also receive regular updates to improve performance and security.
It’s important you use the latest version of iOS or Android to reduce the likelihood of a security breach.
Remember to perform operating system updates over Wi-Fi, because they can use up two gigabytes of data to download.
- On iPhone, go to Settings > General > Software Update.
- On Android, go to Settings > System > Advanced > System update > Check for update.
5. Use 2-factor authentication where possible
You’ve probably heard of 2-factor authentication (also known as 2FA). Essentially, it means using two methods of authentication when logging into something. Generally, these two factors are your password and a unique code sent to your phone.
This unique code can be sent either via SMS, or via a push notification using a 2FA app on your phone. Using a 2FA app is generally considered more secure than receiving authentication codes over SMS. This is partly because SMS codes can be read from the notification on your lock screen, unlike authenticator app codes, which you’ll need to unlock your phone to view.
2FA might not seem all that important for mobile phones, since nearly all apps leave you signed in by default. However, most of your accounts can also be signed into from the web, which is where 2FA helps to improve your security.
Generally, 2FA can be enabled on your Apple/Google account, payment apps (like PayPal), social media and messaging apps, and cloud storage apps (like Dropbox).
To set up 2FA, you will need to go to the settings page on your app, and then go to security settings. Then you will need to set up 2FA through your authenticator app or via SMS.
6. Be careful with public Wi-Fi
While public Wi-Fi is a lot more secure than it used to be, it’s not the most secure way to connect to the internet.
It’s still possible for public Wi-Fi to expose you to security risks. Hackers can theoretically intercept your traffic, and it’s also possible for the Wi-Fi provider to see your browsing history.
If you need to use public Wi-Fi, take the following precautions:
- Only connect to password-protected public Wi-Fi. Networks where you login without a password and then have to sign in through your web browser are generally fine to use.
- Only connect to Wi-Fi providers that you trust. For example, large hotel chains and McDonald’s Wi-Fi should be more secure than networks hosted by small businesses without a dedicated IT security department.
- Never do anything involving highly sensitive data, such as internet banking.
- Consider using a VPN to protect your privacy.
In truth, public Wi-Fi should really be used as a last resort. It’s best to use your 4G if possible, especially for activities involving sensitive data.
7. Avoid using public charging ports
Public charging stations seem great in theory – they allow you to charge your phone on the go, which is very useful when travelling.
The problem is, USB ports can also transfer data, as well as charge your phone – and when you plug in your phone, you have no way of knowing what the USB port is doing.
This means that public charging ports could theoretically transfer malware onto your phone. It’s even possible for hackers to leave behind USB cables with malware installed in public places, waiting for someone to use the cable and infect their phone with a virus.
While it’s best to avoid public charging equipment, it’s still safe to use public power outlets with your own phone charger and charging cable.
8. Don’t transmit sensitive data over HTTP (use HTTPS instead)
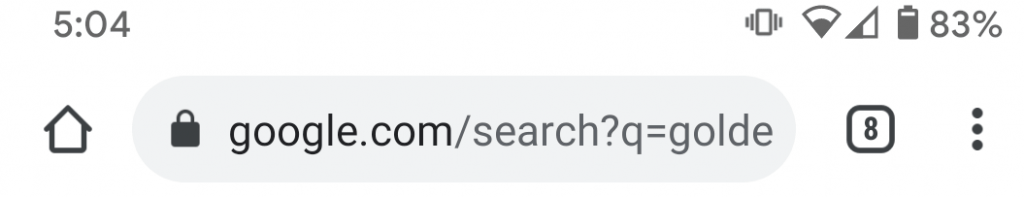
When you visit a website, your browser will try to use a connection protocol known as “HTTPS”. This is the most secure way to connect to a website right now.
You can tell you’re using HTTPS because the browser will typically display a padlock symbol, which looks like this:
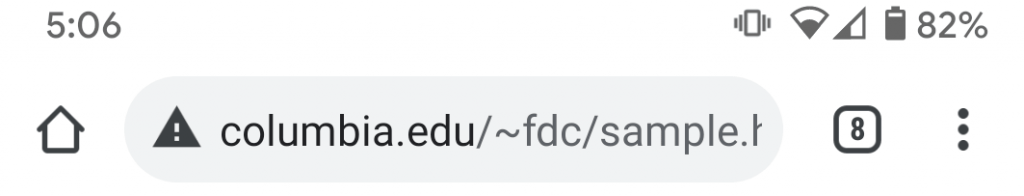
However, sometimes the website won’t have HTTPS set up, and your browser will connect via HTTP instead. HTTP is essentially a less secure version of HTTPS.
You can tell you’re using HTTP because the browser will display a warning symbol, which looks something like this:
Essentially, when using HTTP, it’s best not to transmit any highly sensitive data. This is because traffic transmitted over HTTP is not encrypted, meaning it’s more likely to be intercepted by hackers.
9. Audit your app permissions
If you have a lot of apps installed, especially from small, less reputable developers, it’s a good idea to keep a close eye on the permissions you grant your apps.
Some apps will ask for permissions that they don’t really need. For example, if an app has your permission to use the phone camera, it could theoretically begin taking photos or recording video at any given moment.
Fortunately, on modern smartphones, you can easily see which permissions each app has.
- On iPhone, go to Settings > Privacy, and tap a service. Then you can view the apps that have permission to access or use that given service. You can also set it so that apps can only be accessed when the app is open, which is handy if you have an important app that needs to use your microphone, but you don’t want it recording all the time.
- On Android, go to Settings > Privacy > Permission manager, and select a category. Similar to on iOS, you can see which apps have each type of permission. If you want an app to have a certain permission, you can grant it all the time, only when the app is open, or only when asked.
10. Learn to avoid phishing attempts and scam calls
As a smartphone user, you need to remain vigilant to avoid hackers’ attempts to get you to share sensitive information, using methods such as phishing and scam phone calls.
Phishing is when a hacker gets you to log in to a fake application or website via a link they’ve sent you. Rather than the website signing you into the real application, your login details are sent straight to the hacker, via a fake login form.
With smartphones, you might also receive fraudulent calls from people pretending to be a representative of a large organisation. These scam calls typically ask for sensitive personal details, or for payments to be made.
For example, someone might call you pretending to be from your bank, saying that your account has been used fraudulently. They will later ask for your bank account details in order to help solve the problem, and then steal money from you at a later date.
“Social engineering” is one of the most common ways for hackers to access your data. In fact, a third of all cybersecurity breaches involve phishing.
Here are some tips you can use to avoid scammer’s attempts to manipulate you into sharing sensitive data.
- Never login to a website after clicking on a link in an email. Always navigate to the website separately.
- If you see an email offering you something for free, or asking you to log in to something, delete it immediately, and do not click any links it contains.
- Never share sensitive details with an organisation that calls you out of the blue. Always hang up if the call is suspicious, and call back the organisation through their official customer service line if you think the call may be legitimate.
- Never respond to text messages out of the blue from organisations requesting a call back. Legitimate businesses and government bodies do not send out messages requiring a response via text message. If you’re concerned about the message and think it may be legitimate, call the organisation via their official support line and ask if the message is real.
11. Turn off Bluetooth when not in use
Bluetooth on modern phones is more secure than it used to be. However, it’s still theoretically possible for hackers to use Bluetooth to gain access to your phone. Plus, it uses up a small amount of battery, so if you’re not using your Bluetooth all the time, it’s worth turning it off when you’re not using it.
Also, it goes without saying, but if you have Bluetooth on and see an unknown request to pair with your phone, always reject it. Unknown Bluetooth requests could be an attempt by a malicious party to gain access to your phone.
12. Enable self-destruct after 10 failed password attempts (iOS only)
Modern iPhones have a hidden security setting that you can enable to reduce the likelihood of someone accessing your data.
It’s called “self-destruct”. With self-destruct enabled, your phone will completely erase its memory after 10 failed unlock attempts, preventing anyone from getting access to your data.
While you can wipe your phone remotely using the method we discussed earlier, having self-destruct enabled is helpful in case you’re not aware that your phone has been stolen.
IMPORTANT NOTE: with self-destruct enabled, your phone could theoretically be wiped by children playing with the phone, or by anyone else who picks it up. It’s important to have iCloud data backups enabled before turning this setting on, unless you don’t mind losing all your data.
- On iPhone, go to Settings > Touch ID & Passcode > and change the Erase Data setting.
13. Consider using a VPN
When you connect to the internet on your phone, the owner of the network can actually see quite a lot of information about what you do online – even when using HTTPS browsing.
This doesn’t just include public Wi-Fi networks – your internet service provider can also see what websites you visit, including when browsing at home and using your mobile data.
If you’re concerned about your privacy, you could consider using a Virtual Private Network (VPN) app on your phone. With a VPN, your traffic is encrypted and is routed through another network, often in another country, to protect your privacy.
VPNs do generally cost money (about £6-8 per month), and they might slow down your internet a bit. However, for the privacy and security-conscious, using a VPN app can be a good investment to make.
14. Enable USB restricted mode (iOS only)
As a part of the iOS 11.4.1 update, Apple released a new security feature known as “USB Restricted Mode”. Basically, with USB Restricted Mode activated, it’s much harder for someone to access your data by connecting your phone to another device.
Apple released this feature in response to reports that law enforcement agencies and hackers were using special devices to unlock phones and access encrypted data through the Lightning port.
With USB Restricted Mode enabled, after your phone has been locked for an hour, the Lightning port will only provide charging, rather than data transfer capability.
By default, this setting is turned on, however you can verify this by going to Settings > Touch ID & Passcode > USB Accessories.
15. Encrypt your phone’s data
If you have a modern smartphone, your data is automatically encrypted when you lock it – meaning that the information is scrambled temporarily, and cannot be accessed without unlocking your phone.
However, if you have an older phone, you might want to double-check that your phone is encrypted. Otherwise, it might be possible for thieves to access your data if your phone is stolen.
- On iPhone, go to Settings > Touch ID & Passcode and look for encryption.
- On Android, go to Settings > Security > Advanced > Encryption and credentials.
16. Only download apps from the App Store or Play Store
Some websites will advertise apps that you can download to your phone. However, these apps you find online have not been verified by Apple or Google and may not be secure.
It’s best to only ever download apps from the App Store or Google Play Store to improve your security. These apps have been vetted for security flaws (although they’re not always 100% secure).
Fortunately, it’s not possible to download apps from the web on most devices without jailbreaking (on iPhone) or significantly modifying your security settings (on Android).
17. Run a phone security checkup (Android only)
Android users can take advantage of a widget Google has released called Security Checkup.
If you go to the Google Security Checkup page, you can view some basic recommendations to improve security on your phone and Google account more broadly.
The Security Checkup currently tells you:
- Whether any of your passwords have been found in data breaches and need to be changed.
- Whether your recovery email address and phone number need verifying.
- If any third-party apps have access to your data, so you can review and revoke these permissions if necessary.
- Where your Google account is currently signed in from. This helps you check that no-one else has access to your account.
- What other security actions have been taken recently across the Google account.
About the author

Tom is the founder of Green Smartphones. You’ll find him writing about phones on the Green Smartphones blog, or talking about SIM deals and mobile networks on our YouTube channel. He’s the Android expert on the team – currently using a Google Pixel 9, recently upgrading from a very long-suffering Note 20 Ultra. When he’s not working on Green Smartphones, you’ll find him playing football or hiking.